Next to some download links an alphanumeric code is given, with descriptions like MD5 and SHA-1 or SHA-2. What do these mean?
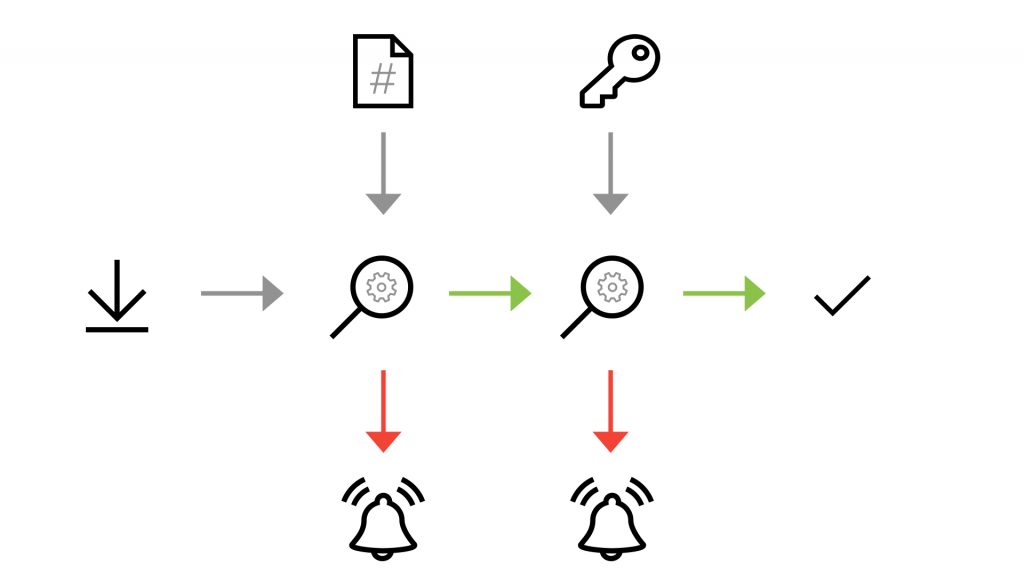
Image 1 Hash and signature verification process for download [8]
The additional information is called a “hash” of the file and it is intended as an integrity check of the file to verify that the file has not been altered or tampered with. For this purpose, it is important that the used function is cryptographically secure, i.e. cannot simply be reversed.
With a known input, in this instance a file, the corresponding hash can be relatively easy calculated. However, if you want to calculate the corresponding input for an existing hash (reversal of the hash function), it must not be easily possible. This is to prevent deliberate “collisions” from being generated. A collision in this case means that a second file can be calculated and generated which shares the same hash value as the original file.
Mathematically speaking, collisions are inevitable as entry values with an arbitrary length will be transformed into hash values with a fixed length. The likelihood of such collisions however, is very small; normally with the construction of such hash algorithms attention is paid to their collision resistance. Furthermore, precautionary measures like the “avalanche effect” were established wherein a slightly changed input generates a significantly changed hash value. This is to prevent an attacker generating an input (or file) which is only subtly different from the original yet sharing the same hash value.
Some known examples of such hash functions are the above mentioned MD5 and SHA (Secure Hash Algorithm). Care must be taken however to only use the methods which are known to be secure at the current time. In the case of SHA-1 for example, practical evidence of the deliberate generation of collisions have been made public [1], which of course undermines the trustworthiness of this hash algorithm. If possible, other methods should be used instead.
Using the Windows operating system for example, the “certutil” program can be used to generate the hash for a file. [2]
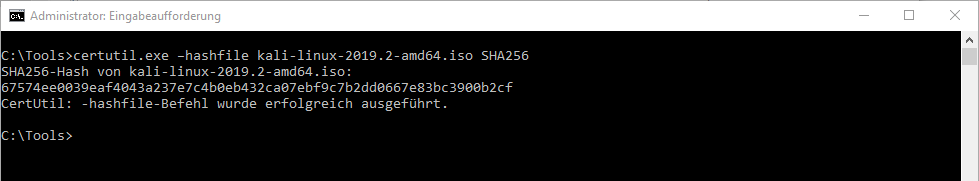
Image 2 Calculating the hash with certutil [2]
A second layer of authenticity of the file is ensured by the GPG (GNU Privacy Guard) key provided by the distributor of the file, utilising the “Web of Trust” to verify whether the key really comes from the stated provider. The authenticity of digital keys is secured by a net of reciprocal confirmations (signatures), combined with the individually assigned trust in those confirmations. The Web of Trust itself has however come under criticism recently. [3]
In our practical example, the signature verification was successful, but the trustworthiness of the keys themselves could not be implicitly determined and should to be verified by the user separately.
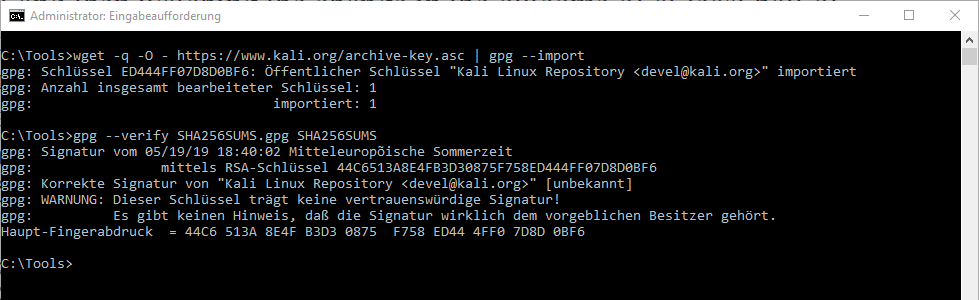
Image 3 Signature verification [9]
In order to easily execute the steps given here some support programs have this type of verification built in to make things simpler for the user. For example, the context menus of 7zip [4] and Gpg4Win-Suite [5] can be used, as they add more entries to the context menu of the file explorer (in Windows operating systems), among which is the option to calculate the hash value.
Another tool is “rget”, similar to “wget” which has been available for a long time, but which carries out an implicit verification. At time of publication however this tool is still under development. [6]
In general, each download should be checked with the steps described above to avoid accidental infection with viruses or other malware. Furthermore, you should generally only download from a trustworthy source and only via an encrypted (https) connection. The actual file as well as the hash values and keys should be originated from separate sources in order to avoid the possibility that an infected file and a matching, but incorrect hash value are being provided from the same source. Currently recommended methods can be found on the website of the BSI (Federal Office for Information Security). [7]
[1] https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html
[2] https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certutil
[4] https://www.7-zip.org/download.html
[5] https://www.gpg4win.org/download.html
[6] https://github.com/merklecounty/rget
[7] https://www.bsi.bund.de/DE/Publikationen/TechnischeRichtlinien/tr02102/tr02102_node.html

Would you like to learn more? Do not hesitate to contact us, we will be happy to help you.


Here you can learn more about our company and our expertise as a pioneer and market leader.