In the area of Industry 4.0, the area of IT security, due to the largely complete interconnection of the systems used in a company, is becoming increasingly important. In this now important business area, the IT security industry offers many solutions to improve the security of the company’s IT systems and infrastructure. [1] Matching the installed software products with a Common Vulnerabilities and Exposures (CVE) database provides an important additional information gathering tool for businesses.
The CVE information is updated approximately every two hours by the National Institute of Standards and Technology (NIST) in collaboration with MITER Corporation. [2] Therefore, it is important to regularly perform a comparison with the installed software. The information gathered about the software products used in this way can be used to improve and support IT security through various application options.
The information contained in a CVE entry may suggest a need for action. This is derived from the description and the risk of self-assessment of a security vulnerability found. The evaluation of the security vulnerabilities found and the resulting risk for the company must be carried out manually, as specific environmental requirements may have to be considered here.
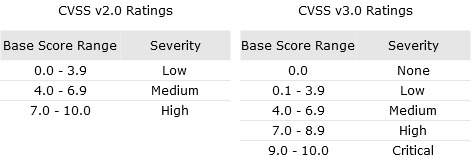
Figure 1: Definition of Criticality of CVSS v2.0 and CVSS v3.0 [3]
The Common Vulnerability Scoring System (CVSS) score included in a CVE record further supports the risk assessment of the vulnerability. This is calculated from the components of the vector string and is used to compare various security gaps. The definition of criticality is shown in Figure 1. Thus, a vulnerability that can be exploited by an attacker only over the Internet, is a low risk for systems without Internet access.
Furthermore, a regular comparison of the installed software products can support the software evaluation. The decisive factor here is not the number of CVEs found, but the assessment of the risk of the software used in a subsequent step. [4] By assessing the risk manually, an assessment can be made as to whether the use of a specific software product poses a high risk or not.
By the regular scan of the own software products and the respective manual estimation of the risk of the found security gaps, the user receives in addition an overall overview over the condition of the software used in a company. This overview can help to steadily expand and improve system-wide IT security.
Various articles in specialist media [5] [6] [7], show the urgency for companies to constantly check the software products used for security vulnerabilities. As a result, preventive measures, against attacks and the resulting, sometimes not inconsiderable consequences, can be planned and implemented.
If you want to learn how a CVE is built and what known examples exist, please read this article: https://www.ondeso.com/en/common-vulnerabilities-and-exposures-cve/
Sounds interesting? Here you can download the summary as PDF for free:
We have briefly summarized all contents in this video for you:
[1] Lass, Sander und David Kotarski: IT-Sicherheit als besondere Herausforderung von Industrie 4.0. Schriftenreihe der Hochschulgruppe für Arbeits- und Betriebsorganisation eV (HAB): Industrie, Seiten 397-419, 2014. https://www.gito.info/homepage/gito/gitoshop.nsf/download.html/1F3E402EB972E145C1257DAF00518C07/$File/lass_IT-Sicherheit-als-besondere-Herausforderung-von-Industrie-4-0_HAB-Tagungsband-2014.pdf, visited 01.10.2019
[2] National Institute of Standards and Technology: NVD Data Feeds. https://nvd.nist.gov/vuln/data-feeds, visited 01.10.2019
[3] National Institute of Standards and Technology: Vulnerability Metrics.https://nvd.nist.gov/vuln-metrics/cvss, visited 01.10.2019
[4] Dombach Ralph, Schmitz Peter: Common Vulnerabilities and Exposures (CVE) CVE & Co. für Einsteiger. https://www.security-insider.de/cve-co-fuer-einsteiger-a-738824/, visited 01.10.2019
[5] Scherschel A. Fabian: CVE-Lagebild 2019: Debian, SUSE, Oracle führen Sicherheitslücken-Rangliste fürs erste Halbjahr an. https://www.heise.de/security/meldung/CVE-Lagebild-2019-Debian-SUSE-Oracle-fuehren-Rangliste-fuers-erste-Halbjahr-an-4505425.html, visited 07.10.2019
[6] Olivia von Westernhagen: Gefahr für Industrieanlagen: Siemens schließt Lücke in Controller-Software. https://www.heise.de/security/meldung/Gefahr-fuer-Industrieanlagen-Siemens-schliesst-Luecke-in-Controller-Software-4467099.html, visited 14.10.2019
[7] Olivia von Westernhagen: Patchday: Microsoft sichert Windows und Browser gegen Angriffe ab. https://www.heise.de/security/meldung/Patchday-Microsoft-sichert-Windows-und-Browser-gegen-Angriffe-ab-4549555.html, visited 14.10.2019

Would you like to learn more? Do not hesitate to contact us, we will be happy to help you.


Here you can learn more about our company and our expertise as a pioneer and market leader.