Just like last year, we would like to take a closer look at the current status report on IT security in Germany [1] from the German Federal Office for Information Security (BSI) and have summarized the most important implications for the industrial environment for you.
Survey period June 2019 – May 2020
At the beginning of the Corona crisis in the period March to May 2020, there was a slight decrease in malware attacks, which could give the impression that the malware producers also experienced a break due to a lockdown. Or maybe they just used the time to strike harder afterwards. According to Arne Schönbohm (livestream of the press conference) there was probably a significant increase in malware attacks after May 2020, which will be shown in more detail in the 2021 report.
Among malicious programs, ’Emotet’ in combination with ’Ryuk’ ransomware is still the frontrunner.
Here you can see how the attack path can work (German only):
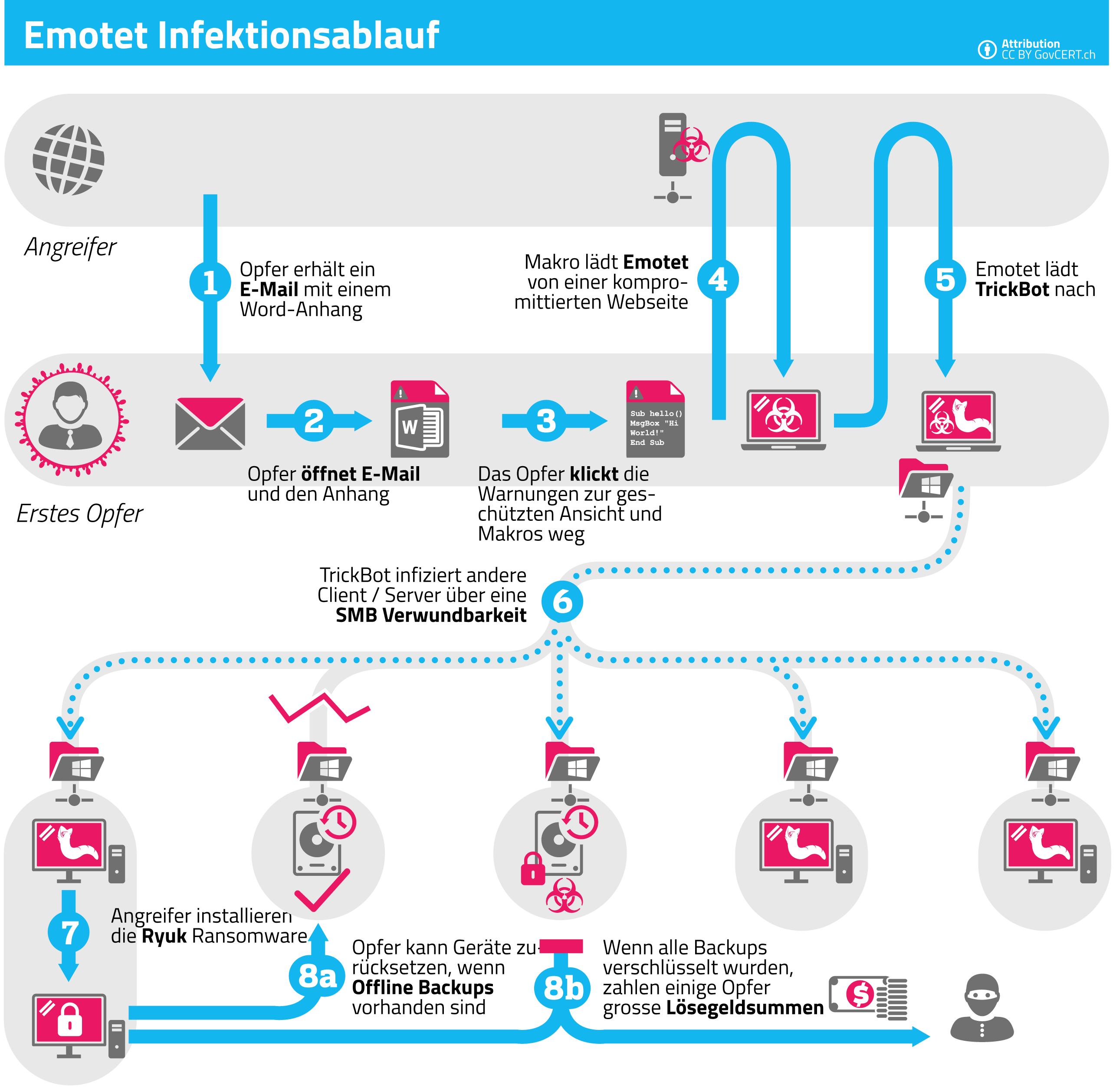
Picture: GovCERT.ch [2]
However, the approach of the attacks has changed. Compared to the previous year, about 15% more https is used to strengthen the trustworthy impression. The perpetrators are acting increasingly targeted and explicitly select their victims, mostly financially strong objects. This results in data leaks in a wide range of industries, even including medical data.
The attackers combined a wide variety of methods in their attacks in order to cause as much damage as possible. These range from social engineering and reloading malware to spying on information and classic SPAM mails with worm-like propagation. In the telecommunications sector and at suppliers, for example, APTs (Advanced Persistent Threats) are predominantly used to collect information, such as access data, from companies that are not so well protected and then to launch attacks on the actual, well-protected target.
Distributed Denial of Service (DDoS) attacks are also becoming more specialized. The attack strategy usually deals with dedicated facilities or dates such as Cyber Monday or Black Friday. Perpetrators are also now responding specifically to victims’ countermeasures. Via so-called ‘carpet bombing’, in which many smaller attacks are launched against many different end devices in the target segment, an attempt is made to undermine existing protective mechanisms against DDoS attacks.
Social engineering campaigns increasingly make use of the time pressure of a current situation or current topics. The COVID-19 pandemic is a plausible example: The population was facing a lockdown. Money was an essential issue, which is why the cards “emergency aid” and “short-time allowance” could be played very effectively for such purposes. In addition, the supposed surge in digitization increased the attack surface here, since significantly lower protective measures often take effect in the home office, which were also usually only implemented pragmatically and quickly, without extensive planning.
Unchanged from the last few years, vulnerabilities are of course still being exploited, because many companies do not bother to fix software vulnerabilities that are critical. Even with an update that has already been made available, according to the observations of the BSI, it is only applied with delay or not at all. Therefore, it is especially recommended to close the vulnerabilities named “Bluekeep” and “Dejablue” and to activate RDP only where it is urgently needed. Since Windows 7 has been discontinued and security updates are only available for customers of the paid “Extended Security Updates Program”, protective measures should also be implemented promptly for future threats.
Hardware vulnerabilities have been in focus especially since 2018, through ‘Spectre’ and ‘Meltdown’. They are very difficult to eliminate because physical properties cannot be fixed by a patch. Only mitigating measures are possible, but often lead to performance, functionality and other losses. Attacks are also possible in this area. They are very complex but can be profitable and have therefore remained interesting.
In the KRITIS (Critical Infrastructure) environments, the technical measures were largely well implemented. In the case of organizational measures, some processes have not yet been adopted or implemented by management. Here, too, the COVID-19 crisis did not go unnoticed. The on-site audits to prove implementation of the BSI Act could not take place in some cases, and the reminder system for this was temporarily suspended (for 5 months). However, the recommendations of the BSI and the Alliance for Cyber Security on the secure home office were worked out and a sustainable change in the way of working and adaptation to the requirements initiated by COVID-19 is expected.
A total of 419 reports were submitted to the BSI during the survey period. In principle, implementation and IT security standards are very heterogeneous in the KRITIS sector. A large proportion of the reports came from the healthcare sector. The remaining reports were distributed almost evenly among IT/telecommunications, energy, finance & insurance and transport & traffic. The majority of reports were due to technical failure, as you can see from the following overview.
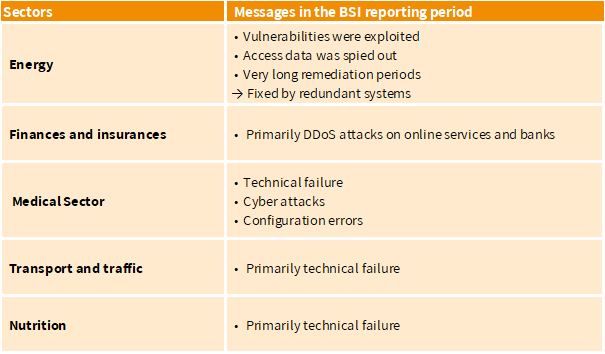
However, the medical sector has other essential tasks than implementing IT security standards. It is increasingly using information technology and should be able to rely on the basic and secure use of IT systems, which is why there is still a need to catch up in this area, but this is supported by accompanying measures, e.g., by the BSI.
The main topics for identified risks from UP KRITIS were vulnerabilities or missing security patches and Advanced Persistent Threats (APTs). Therefore, UP KRITIS dealt more intensively with suppliers and manufacturers regarding their requirements (e.g. security patches).
When using AI systems, there is an important need for action regarding the reliability of security features in addition to topics such as transparency, explainability of decisions and non-discrimination. This is a decisive factor in acceptance by industry and society, because AI systems can be manipulated in some cases without this being immediately apparent to the user. It may even be possible to draw conclusions about sensitive training data from decisions made by the systems.
COVID-19 was certainly an important trigger for digitalization. IT security is thus becoming one of the most fundamental requirements for modern ways of working: ’Information security is becoming a quality feature of digitization “Made in Germany”‘. Constant, dynamic adaptation is necessary, as attackers also react spontaneously and flexibly to current circumstances (such as COVID-19). The BSI also urgently recommends performing backups.
You can read our summary of the 2019 IT security status report again here:
Status of IT security at the shop floor in 2019
[1] https://www.bsi.bund.de/DE/Publikationen/Lageberichte/lageberichte_node.html

Do you not only want to witness our growth but also participate in it? Then have a look at our job vacancies.

Find out more about our products and services for operating and securing of IT components in OT infrastructures.

Do you also want to become an ondeso partner and to get the shop floor fit for future with the help of our products? Click here to read more.