Digital attacks on the German industry cause damages amounting to billions annually. With the right measures, the risk can be significantly reduced.
Machines and systems are increasingly at risk of being infected with viruses or becoming victims of cyberattacks. According to the industry association Bitkom, more than two-thirds (69 percent) of all industrial companies in Germany have fallen victim to digital economic espionage, sabotage, or data theft in the past two years. The overall economic damage is estimated to be in the range of two to three-digit billion sums.
1. Introduction of malware via removable media and external hardware
2. Infection with malware via the internet and intranet
3. Human error and sabotage
4. Compromise of extranet and cloud components
5. Social engineering and phishing
6. (D)DoS attacks
7. Internet-connected control components
8. Intrusion via remote maintenance access
9. Technical malfunctions and force majeure
10. Software and hardware vulnerabilities in the supply chain
Here you will find a summary of the 2023 situation report on IT security published by the BSI, which provides a comprehensive overview of threats in cyberspace.
When it comes to IT security, it’s about confidentiality, integrity, and availability – with availability (alongside quality and efficiency) being paramount in production environments. With the following measures, you can ensure a high level of protection.
While technical security vulnerabilities in hardware and software are regularly exploited to place and propagate malicious code internally, the main entry point for overcoming corporate boundaries is the human factor. Over 90 percent of attacks occur via email, often accompanied or initiated by social engineering. Employees are cleverly manipulated to obtain sensitive information, which is then used to introduce malicious software onto company computers and can spread from there into production.
So don’t focus solely on technical security measures, but think about the people in and around your company. While they may be part of the risk, they are also the most important part of the solution!
![]()
It may be hard to believe, but the most important tip sounds trivial: Promote common sense. Remind your employees that nobody has something to give away for free. Emails with tempting offers are always suspicious. Caution is also advised with unknown contacts or unsolicited email attachments – even from known people.
Furthermore, if a system behaves obviously incorrectly, ceases to function, or changes are detected within the system, employees must report this. Define the responsibilities and accountable individuals for this purpose and communicate them within the departments.
![]()
Next important point: Don’t be too rigid. Security measures can be obstructive, and when things become too complicated, employees look for workarounds. For example, if necessary files cannot be transferred to company computers because USB ports are locked, employees will try to send them via email. If that’s not possible because the mail server blocks potentially dangerous attachments, they will rename the files or try to download them from the cloud. This promotes risky behavior.
It is better to adapt security measures to the requirements of daily work. In the example above, this means that a 70 percent USB safeguard accepted by employees (e.g., by providing a gateway PC with malware scanning) may be more secure than a 100 percent USB block, which would lead to the search, establishment, and secrecy of workarounds.

ondeso DC allows the secure use of USB storage media in the production environment, including testing, permissions and logging.
![]()
Eliminate obvious but popular vulnerabilities such as default passwords on devices or auto-login without password protection with administrative rights. Such unknown user accounts should not be reused out of convenience.
Avoid account sharing, which involves sharing access of an employee with other users, as they may lack permissions or sufficient expertise. Such shared accounts may also spread uncontrollably within the company (‘let the apprentice take a look…’).
Appeal to the sense of responsibility of the employees. If something is misconfigured with the shared account of colleague X – perhaps even intentionally – they will have to justify and prove that another user was responsible for the change.

Discover how our OT Configuration Management Software can quickly and reliably implement compliance requirements and security policies.
![]()
A solid foundation for a strategic approach is the PDCA model (Plan, Do, Check, Act), as implemented in the BSI Basic Protection Compendium, for example. In simplified terms, the process can be broken down into the following steps:
1. Step “Plan”
In the first step, “Plan,” the focus is on structural analysis: What hardware and software are present in production, and in what condition are they? A good asset management system assists here. Next comes the determination of protection requirements. Vulnerabilities are identified, and the need for measures to secure them is established. Subsequently, a decision is made regarding which measures can meet the protection requirements and what their advantages and disadvantages are. For instance, a zone firewall protects against external attackers, while a client firewall further enhances protection against lateral spread. However, firewall rules can also complicate desired communication. Ultimately, only through current software and operating system updates can vulnerabilities be permanently addressed.
2. Step “Do”
In the “Do” step, the focus is on implementation. In addition to infrastructure measures such as network zoning, it is also essential to ensure secure operational processes for OT devices and their software, and to establish concepts for backups for recovery (e.g., after ransomware attacks), software distribution, and patch management.
3. Step “Check”
The “Check” stage involves a (remaining) risk analysis and further security measures. Risk is determined by the probability of occurrence multiplied by the impact. If the probability of occurrence and the impact are so low that further securing exceeds the expected damage, additional security becomes meaningless. Likewise, the implemented measures must be tested for effectiveness. For example, a backup only makes sense if it can be restored, and the system can be returned to a safe state afterward.
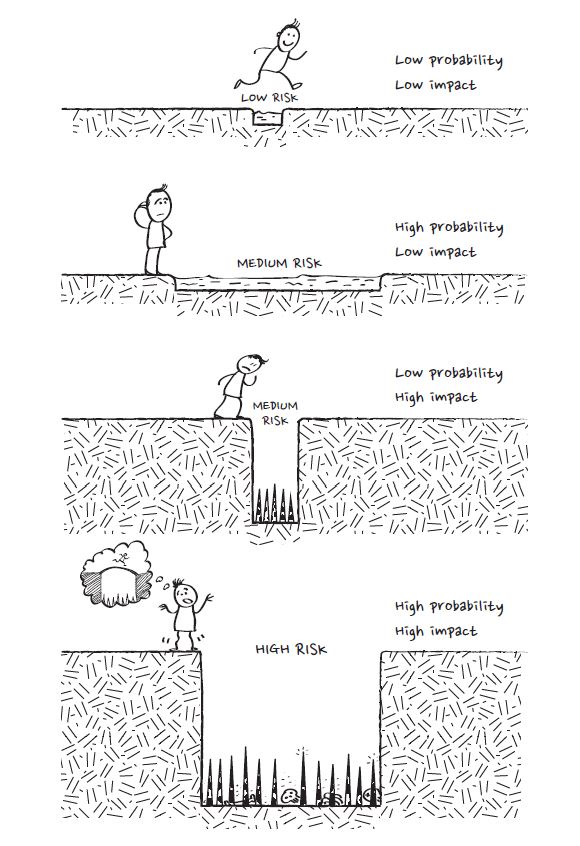
Source: christianespinosa.com
4. Step “Act”
The “Act” phase involves continuous improvement because cybersecurity is an ongoing process that never ends – an everlasting cat-and-mouse game between fortification and attacker. Complete security cannot be achieved.
Therefore, a process must be established that creates the necessary awareness for everyone involved. For new devices, default passwords are changed during commissioning, unnecessary services are disabled, and unnecessary programs are uninstalled.
If you want to involve maintenance even better and also include entire OT systems or deeper layers of the Purdue Enterprise Reference Architecture (PERA levels), there are alternative approaches such as the Layered Blueprints model, specifically designed for production environments. You can find a comprehensive collection of links on the website of the Federal Office for Information Security (BSI).
The best chances lie with those who proactively implement measures consistently and, if necessary, can also react promptly – even in the worst-case scenario with the restoration of a recent backup. Specially developed software solutions can support you in this endeavor.
A proven and globally tested example of this is our Industrial IT Management platform ondeso SR. With it, you can easily configure and automate tasks such as patching clients, creating backups, and distributing current software. We also provide a suitable tool for industrial companies for the data transfer of non-process-related data with ondeso DC.

Protect your OT clients in your production now and test our all-in-one software ondeso SR free for 30 days.

Here you can learn more about our company and our expertise as a pioneer and market leader.


Would you like to learn more? Do not hesitate to contact us, we will be happy to help you.