Did you know that cybercrime generates more money than the international drug trade – and has been doing so for ten years? The cost of industrial espionage in the German economy is estimated at 11.8 billion euros, and statistically, every second company has already become a target of hackers in recent years. [1]
An investment in the information security of one’s own company is therefore indispensable. But in order to know what measures to plan to prevent and defend against an attack, it is first important to learn about the approach of cybercriminals. One strategy that is frequently used is the so-called Cyber Kill Chain model.
This article will provide you with the most important information about it.
The Cyber Kill Chain originated from a military attack model called “F2T2EA” [2].
The model was adapted by Lockheed Martin for information security and called Cyber Kill Chain* [3]. The method was developed to provide companies with a guideline on how to identify, prevent or neutralize attacks before they can cause irrevocable damage. It describes the procedure of a perpetrator who is planning or carrying out a cyber attack on your company.
In the following, we will explain the individual steps and proposed security measures according to the Lockheed Martin model in more detail.
The attack model represents a complete “kill chain”, i.e. an attack chain of a successful attack. The substeps of this attack model are also referred to as IoC (Indicators of Compromise).


The first step for hackers is to search for suitable attack targets. To do this, they collect information about possible victims over a longer period of time by searching platforms such as Google, social media or normal company websites. This collected data is then processed for attacks. If they find vulnerabilities, for example (see CVE article), they can exploit them.
Active reconnaissance describes the process in which data is not just “silently” collected, but actively intercepted. Among other things, social engineering is used to exploit human components in order to obtain security-critical data and insider information. “Deepfakes” are also used to obtain access data, for example.
The tools used here are by no means unknown, and many of them are also used for completely legitimate purposes. To name a few examples: Nmap for network and port scans, OpenVAS for checking for known vulnerabilities (CVEs), and DNSMap, sqlmap and SMBMap for checking the respective services. This list is not final, but should give an approximate impression of the possibilities that are used. The German “Hacker Paragraph” § 202c StGB must also be observed here.
Furthermore, self-developed tools for finding potential targets (so-called “crawlers”) can be used and information from various sources such as the darknet can be used to exploit leaked information, for example.
It is almost impossible to detect reconnaissance at the time of execution. However, you can collect website visitor logs for alerts and historical research, and work with web administrators to leverage their browser analytics. Using this data, you can identify browsing behaviors and prioritize defenses for groups of people and technologies.

As a second step, attackers will prepare their “weapons” and specifically search for vulnerabilities within the entire company through which they can then strike.
In doing so, they sometimes make use of easily accessible “out-of-the-box” solutions. If even more effort is spent on preparation at this stage, information materials for creating your own tools are also relatively easy to access. Building or renting botnets for temporary or permanent attacks is also a popular tool of choice. In addition, there is of course still a black market for so-called zero-day exploits, which are not yet known to the general public and can be exploited by the attacker.
During this phase, you can only defend yourself to a limited extent. Nevertheless, perform analysis to understand current malware artifacts and create procedures for early detection. Collected files and metadata can be used to perform future analysis and detect novel attacks.
To do this, familiar tools can be built and used:
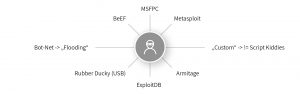

After a target has been selected and all “weapons” have been prepared, the active attack starts – the malware is going to be delivered. Here, the “usual” communication channels via emails or via USB storage media are often used.
The attacks are usually camouflaged as “typical” files, such as application documents or invoices. Often, human error (e.g. USB sticks with the inscription: “Salary slip”, “Private pictures”, …) are exploited. But also prepared websites (e.g. waterholing, drive-by download, …) can distribute hidden viruses or spread malicious files.
From this level, you can actively defend against attacks for the first time. To do this, it is first necessary to analyze which transmission media are used for intrusion attempts and which servers and persons are targeted. By using the artifacts of the weapon system, new payloads can then be detected at the point of transmission. In addition, technical protection measures for the use of USB storage media (see ondeso DC) could increase security.

Once the malware has been delivered, the attacker will exploit vulnerabilities to gain full access to your corporate network in later steps. This can be done “silently” by only scanning the target of evaluation, but it can also lead directly to an active influence on the productive systems.

Regular patching and automatically executed vulnerability scans of your own hardware and software are key here. User training and email phishing tests for employees, as well as training on secure software development, should also not be neglected.
Once the attacker has inspected and researched his system of evaluation, he will begin to persist his malware, as well as access to the system. Popular methods include creating backdoors in existing programs or using a reverse shell to execute commands on the affected device. Communication with the device can take place in a variety of ways; more on this in phase 6.
If the attacker then has long-term access to your system – this is known as an “advanced persistent threat” (APT) – it is easy for him to expand to supplier and customer networks or to infiltrate further parts of your own network.
Here, with the help of implemented security solutions, it is necessary to recognize and log the installation processes and to create new security measures with the help of these analysis. Understanding the required administrator or only user rights and restricting those can make certain attacks more difficult.

Since the attacker now has permanent access, he can initiate specific actions and, for example, establish a connection to CC servers to obtain further instructions, malware or updates from there.
In this phase, you can try to prevent communication to known CC servers, for example, by disabling connections to botnets, or, as mentioned in previous steps, monitor your own traffic or data volume and enable alerts when thresholds are exceeded.

The longer an attacker has access to the systems, the greater the impact can be. Examples include encryption or the publication of documents and their manipulation. As proven in the past by Stuxnet and Co, not only office environments but also production processes are at risk, as these can be negatively influenced in a targeted manner. As a result, not only daily business is threatened, but also the entire existence of the company could be at stake.
Among other things, the use of IT forensics can help in the evaluation and reconstruction of the attack.
Finally, we would like to point out once again that this article deals with exemplary security measures according to the attack model by Lockheed Martin. Which measures are most suitable for your company and your specific use case always depends on the actual circumstances, such as the threat situation, scope and relevance of your system.
The basic principle is: Prevention instead of reaction!
In advance, your own environment should be analyzed and assessed in a structured manner in order to be able to keep a cool head both in a “normal case” and in an “emergency”. Of course, you can also consult experts.
In addition, an emergency plan should be developed and tested in the event of an emergency. Here, you should note that an emergency plan is only possible if transparency regarding the security risk has been created in advance. The following downloads are worthwhile for your company:
International sources:
National sources (Germany):
If you need assistance in securing your production, feel free to contact us!
*Cyber Kill Chain is a registered trademark of Lockheed Martin Corporation.
Sounds interesting?
Here you can download a summary as PDF for free:
We have also briefly summarized all the content for you in this video:
[2] Hutchins, Eric M. ; Cloppert, Michael J. ; Amin, Rohan M.: Intelligence driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. In: Leading Issues in Information Warfare & Security Research 1 (2011), S. 80
[3] https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
[4] https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
[5] https://www.enisa.europa.eu/publications/industry-4-0-cybersecurity-challenges-and-recommendations
[6] https://www.enisa.europa.eu/publications/guideline-on-security-measures-under-the-eecc