Not all IT is the same. The IT used in the industrial environment differs significantly from that used in the office environment. Particularly with the increasing networking in production triggered by Industry 4.0, Industrial IT is changing with rising speed. Digitalization is advancing, and with it comes a multitude of new standards, solutions, projects, abbreviations and technical terms that you should definitely be familiar with in the production environment in order not to lose touch. We have already summarized some of these terms for you and explained them with short definitions and references in the following article.
Asset Administration Shell
Together with the physical asset, the administration shell represents the image of the Industry 4.0 component. The administration shell contains the “virtual digital and active representation of an I4.0 component in the I4.0 system”1, where “administration shell […] is used as a synonym for asset administration shell (AAS)” 2.
In it, “static characteristics, parameters, methods, capabilities, operations, states and many other things”1 are expressed in a standardized form and can be accessed via it – but possibly not by everyone in the value chain or even within the same organization. Depending on the risk assessment, security protection goals should also be maintained there.
Interested parties can take a closer look at files with the AASX Package Explorer3 and there are also some examples4.
Image: GitHub
1 https://www.bmwi.de/Redaktion/DE/Publikationen/Industrie/industrie-4-0-verwaltungsschale-in-der-praxis.pdf?__blob=publicationFile&v=6 (s. 11, 2.2)
2 https://i40.iosb.fraunhofer.de/FA7.21%20Begriffe%20-%20Industrie%204.0#verwaltungsschale
3 https://github.com/admin-shell-io/aasx-package-explorer
4 http://www.admin-shell-io.com/samples/
Application Whitelist
An application whitelist is a collection of program components (executables, DLLs, libraries, configuration files, etc.) that have been granted permission to run on a computer by a user or administrator.
Application whitelisting solution (abbreviation: AWL), application control program or application whitelisting technology refers to the program used to enforce an application whitelist on a computer1.
1 “Application Whitelisting in der Industrie“, Klaus Jochem (2020) – https://klausjochem.me/
Bundesamt für Sicherheit in der Informationstechnik
(English: Federal Office for Information Security)
The BSI’s task is to “preventively promote information and cyber security in order to enable and advance the secure use of information and communication technology in our society.”1
It provides, among other things, important information for both private and commercial users, such as the IT basic protection catalog with the important IND module for industrial environments.
1 https://www.bmwi.de/Redaktion/DE/Publikationen/Industrie/industrie-4-0-verwaltungsschale-in-der-praxis.pdf?__blob=publicationFile&v=6 (s. 11, 2.2)
Computer Emergency Response Team
A CERT serves as a central point of contact in the event of security-relevant incidents. Both proactive and reactive measures can be offered. One example of this is preventive measures to protect the system(s) from possible damage. However, support can also be offered in the event of damage that has already occurred in order to achieve limitation or elimination1.
In addition to in-house CERTs, there are also higher-level bodies or institutions that provide the services described, such as the CERT@VDE2 or the CERT-Bund.
Among other things, vulnerability reports are published there so that they can be used to assess one’s own system. In addition, there are also so-called “advisories” which provide recommendations for dealing with the reported vulnerabilities3.
1 https://www.bsi.bund.de/DE/Themen/Unternehmen-und-Organisationen/Cyber-Sicherheitslage/Reaktion/CERT-Bund/cert-bund_node.html
2 https://cert.vde.com/
3 https://cert.vde.com/de-de/dienste
Cybersecurity & Infrastructure Security Agency
American counterpart to the BSI in Germany. Provides information about current vulnerabilities that have already been actively exploited at https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Common Security Advisory Framework
CSAF is a standardized, machine-readable format for the exchange and automated processing of security advisories1. It is intended to support the simplified discovery and evaluation of affected advisories through the automated comparison between manufacturers and operators. In addition to products and vulnerabilities, it also contains information about the severity.
1 https://docs.oasis-open.org/csaf/csaf/v2.0/csaf-v2.0.html
Common Vulnerabilities and Exposures
CVE is the standard for the uniform naming convention and identification of publicly known vulnerabilities in information systems. In this way, vulnerabilities can be communicated internationally across all language barriers. In this process, a CVE is divided into a prefix, a year and a numbering, is firmly assigned and thus offers added value for companies. A well-known example of this is the “BlueKeep (CVE-2019-0708).
A detailed article and a short video summary can be found here:
Common Vulnerabilities and Exposures (CVE)
Edge devices play a key role in the further development of companies towards Industry 4.0. They are intelligent network components that enable access to the core networks of a company or a service provider. They are located at the edge of the network and are becoming increasingly intelligent in order to be able to offer various service options, such as life cycle services (asset management, predictive maintenance, performance management) or process optimization through cloud-based services1, 2. The specialist and provider for these devices is our technology partner Secunet.
Particularly when used in industrial environments, it is important to ensure that the devices are also appropriately designed for the conditions prevailing there.
1 https://tecnews.digital/strategie/edge-devices-als-schluessel-fuer-industrie-40
2 https://www.itwissen.info/edge-device-Edge-Device.html
Enabling Linux in Safety Applications
The ELISA Open Source Project was launched by Arm, BMW Car IT GmbH, KUKA, Linutronix and Toyota. The goal of this project is to develop a set of tools and processes to help companies develop and certify Linux-based safety-critical applications and systems whose failure could result in loss of life, significant property damage, or environmental damage1.
MITRE ATT&CK(R) Matrix for ICS
The ICS matrix summarizes the attack techniques and the procedure for attacking an industrial control system in 12 stages. It covers almost 90 techniques from initial access to the implementation of an attack1. Each of these techniques also provides examples of detection, countermeasures and the tools used.
1 https://attack.mitre.org/matrices/ics/
IEC 624431 is an international series of norms and standards for cybersecurity in industrial automation. The aim is to check potential weak points in control and instrumentation technology and to develop appropriate protective measures. The standard divides the industry into three different entities: Equipment and machine manufacturers, system integrators and plant operators.
The structure of IEC 62443 is divided into the following sections:
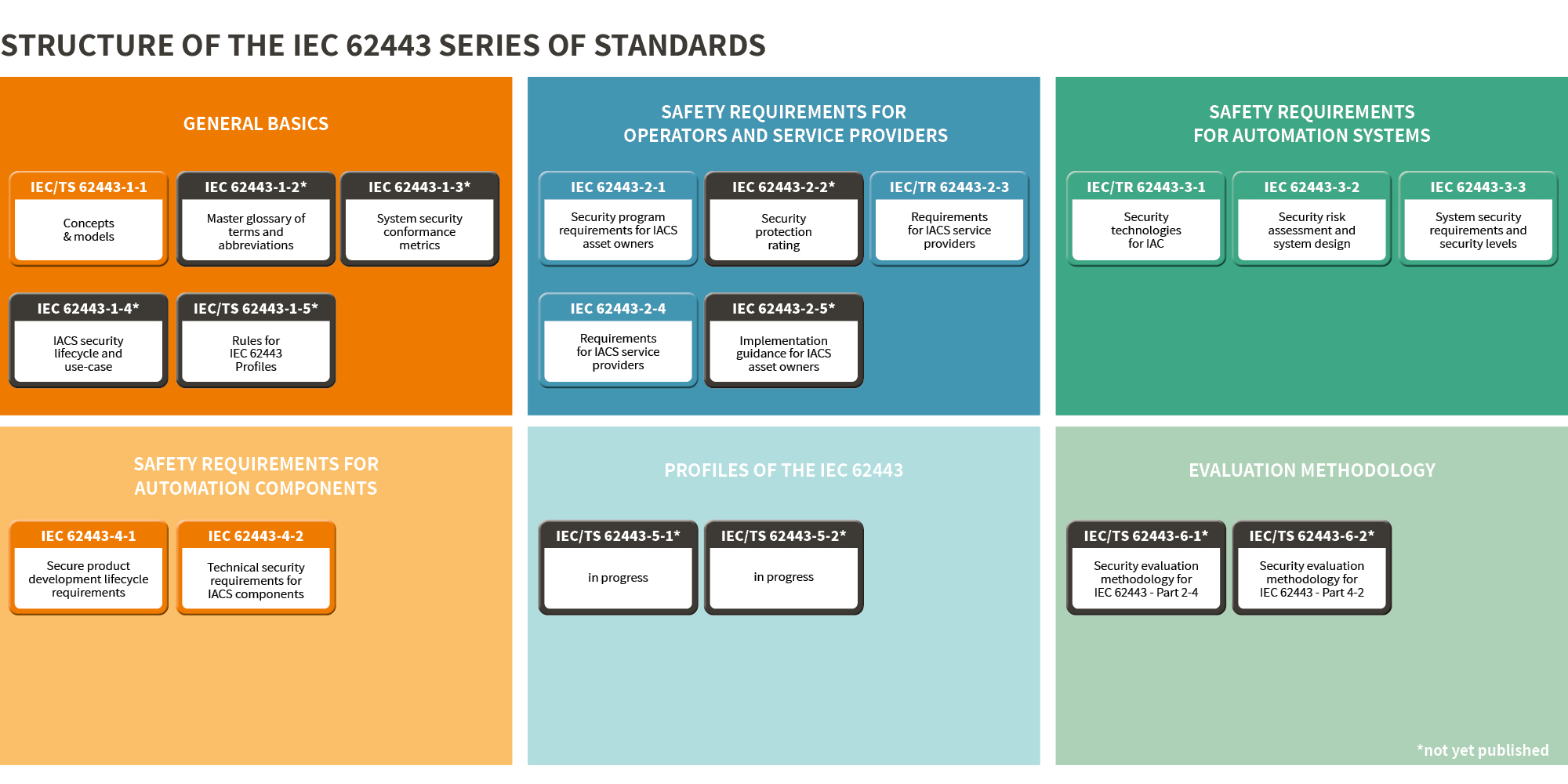
1 https://www.sichere-industrie.de/iec-62443-grundlagen/
Read more about this topic in our article:
IEC 62443-2-3: These manufacturers support the standard
With IT-Grundschutz (IT basic protection)1, the German Federal Office for Information Security (BSI) enables companies to identify and implement necessary security measures in a systematic manner.
Structured into different modules, which range thematically from applications (APP) to networks and communication (NET) to security management (ISMS), it forms the basis for anyone who wants to deal comprehensively with the topic of information security.
The IND layer deals with security aspects of industrial IT. This layer includes, for example, the modules process control and automation technology, general ICS component and programmable logic controller (PLC).
Here is an overview of the security aspects of the IND:
The term “Industry 4.0” was first used publicly at the Hannover Messe in 2011. It was created by Wolfgang Wahlster, Henning Kagermann and Wolf-Dieter Lukas, three representatives from business, politics and industry, and was intended to represent the future of production. The goal was and is to use the latest information and communication technologies in production in order to work more effectively1. The advancing digitalization is also an important factor of Industry 4.0.
In our video “OT for OEM”, we have briefly and succinctly summarized the four stages of the industrial revolution and explain how Industry 4.0 got its name and what new opportunities it presents for suppliers.
Long Range Wide Area Network
LoRaWAN1 is a media access control (MAC) layer protocol for wireless battery-powered systems in a regional, national or even global network. It is based on Semtech’s LoRa modulation scheme and is designed for large public networks with a single operator. The focus is on requirements of the Internet of Things, such as secure end-to-end encryption.
Message Queuing Telemetry Transport
MQTT is an open network protocol for machine-to-machine communication (M2M) developed by Andy Stanford-Clark (IBM) and Arlen Nipper (Cirrus Link Solutions) in 1999. It enables the transmission of telemetry data in the form of messages between devices, which can also be encrypted using the TLS protocol. Even high delays or restricted networks do not pose a problem. This is used, for example, in devices such as sensors, cell phones or vehicles. An MQTT server can additionally be used as a state database1.
1 https://www.embedded-software-engineering.de/was-ist-mqtt-a-725485/
Open Platform Communication Unified Architecture
OPC is a communication protocol for Industry 4.0 and ensures manufacturer-independent data exchange by standardizing access to machines and devices in the industrial environment. OPC UA was published in 2008 and is the current specification of the standard. Older specifications are known as OPC XML, OPC Command or OPC DX1.
The standard has the following goals2:
1 https://www.opc-router.de/was-ist-opc-ua/
2 https://opcfoundation.org/about/opc-technologies/opc-ua/
Operational Technology
The greatly increased demands on quality and productivity in production environments make new IT solutions – especially for this environment – inevitable . Thus, the term OT became more and more familiar. It was defined by Gartner1 as: “Hardware and software that detects or causes change by directly monitoring and/or controlling physical devices, processes and events in the enterprise.”
Find out in this video what matters when it comes to IT operations in OT infrastructures .
1 https://www.gartner.com/en/information-technology/glossary/operational-technology-ot
Learn more about the topic in our two-part Expert Talk:
Building an OT organization: Expert Talk with Max Weidele / Part 1
Building an OT organization: Expert Talk with Max Weidele / Part 2
Patches, updates, and upgrades are often confused because of their similarity. In short, a patch is a bug fix to close a vulnerability. An update, on the other hand, brings a new, smaller function update and can thus provide new features or improve older ones. In the case of an upgrade, a new, revised version is installed.
Read more about this topic in our article:
The history of Microsoft Patch Management
Purdue Enterprise Reference Architecture
The model developed in the early 1990s provides a schematic division of the network into different layers (“levels”), whereby even complex implementations can be represented as an abstracted and thus unified diagram. The division into different layers (“levels”) helps to more easily plan and implement the appropriate measures, e. g. for securing the overall system. Specific attention is paid to the separation or transition between the OT (or ICS) network and the IT network.
However, due to the changed general conditions (IoT devices, direct cloud connection, etc.) since the introduction of the model, there is also repeated criticism of the use of the model, stating that the reference architecture is no longer up to date1, 2.
1 https://www.sans.org/blog/introduction-to-ics-security-part-2/
2 https://www.sichere-industrie.de/purdue-model/
Reference Architecture Model Industry 4.0
RAMI 4.0 provides a three-dimensional layer model as a basic architectural description in the context of Industry 4.0. The description of the properties of the respective assets within the system takes place via the administration shell1 .
In this context, the networked manufacturing plants or the devices they contain are considered and mapped over the entire life cycle from development, through use in production, to disposal/recycling2, 3.
Image: DKE
1 https://www.plattform-i40.de/PI40/Redaktion/DE/Downloads/Publikation/rami40-einfuehrung-2018.html
2 https://www.dke.de/de/arbeitsfelder/industry/rami40
3 https://www.beuth.de/en/technical-rule/din-spec-91345/250940128
System hardening describes the process of reconfiguring IT systems and applications to better protect against attacks. For example, new password policies can be introduced, or outdated protocols can be disabled. Uninstalling or disabling unused software and services is also part of system hardening. For Windows 10 devices, for example, there is a hardening guide from the BSI called “Projekt SiSyPHus”1.
This guideline describes how the information security of automated machines and systems can be achieved by implementing concrete protective measures; for this purpose, aspects of the used automation devices, automation systems and automation applications are considered.
Based on a common definition of terms agreed between manufacturers of automation devices and systems and their users (e. g. machine builders, integrators, operators), a uniform, practicable approach is described as to how information security can be ensured throughout the life cycle of automation devices, systems and applications. The life cycle considers the phases of development, integration, operation, migration and decommissioning.
The guideline defines a simple process model for processing and presenting information security. The model consists of several process steps1.
A virtual patch does not repair the actual faulty application but establishes an additional security mechanism – sometimes upstream – which is intended to prevent the exploitation of a vulnerability. A “classic” patch, on the other hand, fixes the cause of the problem and does not combat or mitigate its effect.
Further information and a comparison of the advantages and disadvantages of virtual patching can be found here:
Article: Virtual Patching – curse or blessing?

We are constantly expanding this list and would be happy to add your term as well.
* ondeso is actively committed, together with all employees, to prevent and eliminate discrimination. General technical terms and foreign words are therefore not related to our values and guiding principles, they are only used for technical understanding.
https://www.bmwi.de/Redaktion/DE/Publikationen/Industrie/industrie-4-0-verwaltungsschale-in-der-praxis.pdf?__blob=publicationFile&v=6 (s. 11, 2.2)
https://i40.iosb.fraunhofer.de/FA7.21%20Begriffe%20-%20Industrie%204.0#verwaltungsschale
https://github.com/admin-shell-io/aasx-package-explorer
http://www.admin-shell-io.com/samples/
“Application Whitelisting in der Industrie“, Klaus Jochem (2020) – https://klausjochem.me/
https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Grundschutz/Kompendium/IT_Grundschutz_Kompendium_Edition2021.pdf?__blob=publicationFile&v=6
https://www.bsi.bund.de/DE/Themen/Unternehmen-und-Organisationen/Cyber-Sicherheitslage/Reaktion/CERT-Bund/cert-bund_node.html
https://cert.vde.com/
https://cert.vde.com/de-de/dienste
https://tecnews.digital/strategie/edge-devices-als-schluessel-fuer-industrie-40
https://www.itwissen.info/edge-device-Edge-Device.html
https://www.linuxfoundation.org/press-release/the-linux-foundation-launches-elisa-project-enabling-linux-in-safety-critical-systems/
https://www.sichere-industrie.de/iec-62443-grundlagen/
https://www.dfki.de/fileadmin/user_upload/DFKI/Medien/News_Media/Presse/Presse-Highlights/vdinach2011a13-ind4.0-Internet-Dinge.pdf
https://www.lora-wan.de/
https://www.embedded-software-engineering.de/was-ist-mqtt-a-725485/
https://www.opc-router.de/was-ist-opc-ua/
https://opcfoundation.org/about/opc-technologies/opc-ua/
https://www.gartner.com/en/information-technology/glossary/operational-technology-ot
https://www.sans.org/blog/introduction-to-ics-security-part-2/
https://www.sichere-industrie.de/purdue-model/
https://www.plattform-i40.de/PI40/Redaktion/DE/Downloads/Publikation/rami40-einfuehrung-2018.html
https://www.dke.de/de/arbeitsfelder/industry/rami40
https://www.beuth.de/en/technical-rule/din-spec-91345/250940128
https://www.bsi.bund.de/EN/Topics/Cyber-Security/Recommendations/SiSyPHuS_Win10/AP11/SiSyPHuS_AP11.html
https://www.vdi.de/richtlinien/details/vdivde-2182-blatt-1-informationssicherheit-in-der-industriellen-automatisierung-allgemeines-vorgehensmodell

Are we already connected?
Why not take a look at our Linkedin channel?


Here you can learn more about our company and our expertise as a pioneer and market leader.